What is Encryption?
Encryption is a method that encodes the data that is unreadable by unintended parties.
For example we want to send a text “The wardrobe key is on the kitchen shelf” secretly to another peer. This is clear text information and can be read by the hacker easily. With help of encryption we can encrypt this text before sending and any of the middle man/hacker will not be able to identify the real text/data sent.
For example we want to send a text “The wardrobe key is on the kitchen shelf” secretly to another peer. This is clear text information and can be read by the hacker easily. With help of encryption we can encrypt this text before sending and any of the middle man/hacker will not be able to identify the real text/data sent.
The above text will look like like a output of random characters as given below:
“XpgWyZabcd15ulWzaeBPTXuhalDqMYZTxzPOvzySYlajkashfasydoasfkl”
This can only be decrypted by the intended party that posses the key for decryption.
Encryption Algorithms
Many different types of algorithms are used within the IPSec protocol suite. Two common types of algorithms used for encryption are synchronous and asynchronous. A third type of algorithm used within the IPSec protocol suite is a hashing algorithm to provide authentication and integrity for the data. This section looks at the advantages of each type of algorithm and how to use the Diffie-Hellman key exchange to exchange the keys used in each of the processes. Some of the qualities you should look for in a good encryption algorithm are the following:
- Security against cryptographic attacks.
- Scalable, variable key lengths.
- Any change to the clear-text input should result in a large change to the encrypted output
- No restrictions on import or export.
Type of Encryption Algorithms
- Symmetrical Algorithm
- Asymmetrical Alogrithm
Symmetrical Algorithm
A symmetrical
algorithm is defined as a shared key algorithm that is used to encrypt
and decrypt a message. Symmetrical algorithms use the same key to
encrypt and decrypt the message.
Examples of Symmetrical Algorithms
- Data Encryption Standard (DES) – 56 Bit Key
- 3 DES – 168 Bit Key
- Advanced Encryption Standard (AES) – 128 or 256 Bit Key
Advantages of symmetrical algorithms
- They are very fast at encrypting bulk amounts of information.
- The key length is usually 40 to 168 bits.
- Mathematical computations are easy to implement in hardware, so offloading the processing can be done cheaply and easily.
- The sender and receiver share the same passwords. The problem with shared passwords is how to get the key from one device to the other. If the key is sent across an untrusted network, you run the risk of it being sniffed and captured by a hacker. If you phone the technician at the other end, you run the risk of phone tapping. As you progress through this chapter, you will see thatkey management can be a major concern for security.
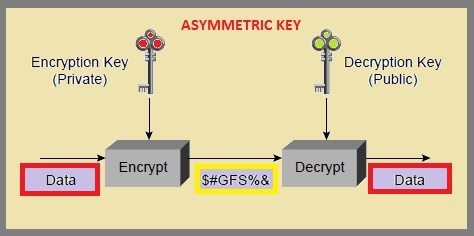
Asymmetrical Algorithm
An asymmetrical
algorithm is defined as an algorithm that uses a pair of keys to
securely encrypt and decrypt a message. Asymmetrical algorithms use one
key to encrypt and a different, but related, key to decrypt.
Examples of Asymmetric Algorithms
- RSA
- ElGamal
- Elliptic Curves.
Advantages of asymmetrical algorithms
- They are great for use in authentication because one key is always private (you are the only one with that key).
- Key management is easier (one key is public to everyone).
- They can be used for digital signatures, authenticated key exchanges, e-mail, or small amounts of data.
- They are based on very hard mathematical equations.
- The disadvantage to the public key system is that it is usually very slow encrypting information compared to symmetrical encryption. Therefore, it is used to encrypt session keys and small amounts of data, such as e-mail messages.