- Home-icon
- Knowledge Base
- _ROUTING
- __ROUTING BASICS
- __RIP
- __EIGRP
- __OSPF
- __ISIS
- __BGP
- __NAT
- __PBR
- __IPv6
- __ROUTE REDISTRIBUTION
- _SWITCHING
- __SWITCHING BASICS
- __VLANS
- __HSRP
- __VRRP
- __GLBP
- __Link Aggregation
- __Port Miroring
- __WIRELESS
- _CCIE SP
- __SEGMENT ROUTING
- __MPLS and MPLS-VPN
- __INTER-AS OPTIONS
- __CSC
- __TRAFFIC-ENGINEERING
- __VPNv6
- __Multicast and M-VPN
- __L2VPN
- __QoS
- __BFD
- __IP SLA
- __TWAMP
- _SECURITY
- __IPSec
- __MACSec
- _TSHOOT
- _SDN
- _INTERVIEW QUESTIONS
- DOWNLOADS
- _IOS
- _WIRESHARK CAPTURES
- _BOOKS
- _CHEATSHEETS
- VIDEOS
- Discussion Forum
- CONTACT
- _Contact Us
- _ABOUT US
- _PRIVACY POLICY
- _TERMS OF USE
- _DISCLAIMER
Useful Articles
25/recent/ticker-posts
Recent posts
View allBGP Messages
BGP Messages BGP exchanges 4 different messages. These message are exchanged by BGP Peers to establish a connection, exchange network prefixes, maint…
READ MORE »BGP Best Path Selection Criteria
BGP Best Path Selection Criteria BGP Best Path Selection Criteria is mechanism in BGP that helps finding the best path to a destination network. Whil…
READ MORE »BGP States
BGP States Understanding of BGP States is important in order to understand How BGP Works. Just like the IGPs EIGRP, OSPF or ISIS, BGP also establishe…
READ MORE »EIGRP Tables
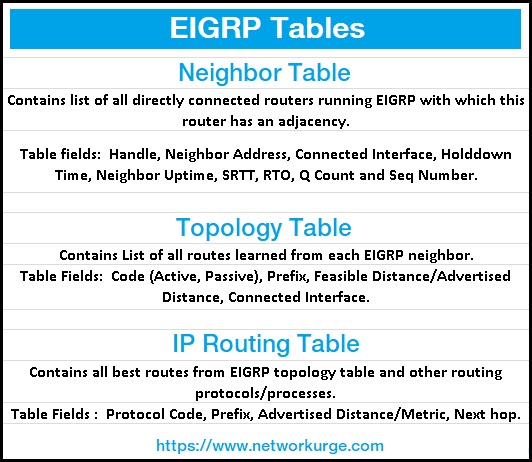
EIGRP Tables Three EIGRP Tables are maintained by EIGRP to execute its operation i.e. Neighbor Table , Topology Table , and IP Routing table for i…
READ MORE »Labels
- Administrative Distance 2
- API 1
- ARP 1
- Basic Route Selection Criteria 3
- BGP 8
- Cabling 2
- CEF 2
- DNS 2
- EIGRP 7
- ENCRYPTION 1
- Fast Switching 1
- HASHING 1
- IGMP 1
- INTERVIEW QUESTIONS 7
- IP 2
- IP SLA 2
- IPv6 6
- ISIS 7
- Load-Balancing 1
- MPLS 2
- MPLS-VPN 3
- Multicast 3
- NFV 6
- OSI Model 1
- OSPF 16
- PIM 1
- Process Switching 1
- Proxy ARP 1
- QoS 1
- RIP 13
- Route Filtering 3
- Route Redistribution 7
- Route Summarization 1
- SD-WAN 2
- SDN 9
- Segment Routing 5
- Source Tree 1
- subnetting 2
- Switching 3
- TCP 2
- TRAFFIC ENGINEERING 2
- Troubleshooting 3
- uCPE 2
- VNF 3
Popular Posts

UTP Cable Color Coding
October 10, 2017

Subnetting Class C
April 27, 2020
Random Posts
3/random/post-list
Popular Posts

UTP Cable Color Coding
October 10, 2017

Subnetting Class B
April 28, 2020

Subnetting Class C
April 27, 2020
Menu Footer Widget
Designed By by TemplatesYard | Copyright Network Urge